INFORMATION SECURITY INSIDER THREAT VISUALIZATION: THEFT OF INTELLECTUAL PROPERTY
1National Research Nuclear University MEPhI (Moscow Engineering Physics Institute), Russia, Moscow
2Financial University under the Government of the Russian Federation, Russia, Moscow
Anthony.Zaytsev@gmail.com, AAMalyuk@mephi.ru
Contents
2. Development of information security insider threat system dynamics models
3. Visualization of theft of intellectual property for business advantages
4. Visualization of theft of intellectual property for business advantages with accomplices.
Abstract
Paper deals with the problem of insider threat visualization. An insider threat classification is adduced, method of visualization of insider threats using system dynamics modeling is considered and forecasting behavioral models for threats of theft of intellectual property for business advantages alone and with accomplices are developed.
Key words: system dynamics, behavioral models, scientific visualization, imitation modeling, insider threat, intellectual property
1. Introduction
Researches in the field of information security in Russia were recently concentrated in outsider threat countermeasures. Therefore there is considerable armory of countermeasures to outsider threats, including standards and best practices, which had undergone some improvement cycles and provide sufficient level of information assurance if implemented right.
Problem of information assets and IT-infrastructure assurance from insider threat does not have solution in technology sphere only and can be solved with the help of organizational measures. In view of this fact, there are no widely accepted common practices to secure information assets and IT-infrastructure from insider threats nowadays.
Information assurance from insider threat is the most complicated problem in information security because it depends on psychological and behavioral aspects, which can be hardly assessed and forecasted by managers. For an instance, manager supposes that sanctioning his subordinate would cause diminishing of the insider threat and quite the contrary it often leads to conflictís escalation and rises the probability of information system sabotage (IT-sabotage). Thus, support of decision for potential insider threat countermeasure with the help of behavioral models is a problem of a very high importance. For effective decisions a manager might surely take the aid of visual information, which is easy to perceive and allows to better understand the dynamics of further trend of potential insider information security incident (if quality of visual information is considerable).
System dynamics is an expedient approach for insiderís behavior visualization [1]. Carnegie Mellon University Software Engineering Institute CERT Insider Threat Team (CERT) firstly applied this approach for insider threats research in 2003 [2]. They collected open-source information about insider threat incidents, developed a classification of insider threats and casual loop diagrams (CLD) for all the classes of insider threats they picked out. The diagrams they created can help better understanding insiderís behavior, but the CLD cannot be used to run simulation and get visual information for further analysis and decision-making.
Independently of CERT system dynamics approach was used as a method for insider threats research in [3]. In this work, one flow diagram (FD) for all classes of insider threats was developed, but this FD also can not be used for simulation and computer visualization.
This paper considers a method of getting visual information about potential insiderís behavior with the help of system dynamics modeling. Forecasting models for theft of intellectual property (IP) are developed and visual information of test imitation is adduced.
2. Development of information security insider threat system dynamics models
A system dynamics modeling of every system including behavior of insider contains of further sequence of steps:
1. Building of a common relationship diagram, which represents interconnections between main elements of the modeling system. At this step, behavior of insider should be studied and the main clusters of factors that influence the dynamics of the insider threat should be figured out.
2. Development of a CLD. At this step, main elements of the modeling system should be considered in details and their relationship should be depicted in form of causal relationship (CR). The aggregation of this parameters and CR forms an oriented graph. CR should be considered as positive if increase (diminishing) of an influencing parameter causes increase (diminishing) of an influenced parameter. If increase of influencing parameter causes diminishing of influenced parameter, CR should be considered as negative. Systemís parameters and CR form casual loops (CL) that determine insiderís behavior. CL can be also divided into positive (re-enforcing) and negative (balancing) according to its influence on systemís behavior. Balancing CL flattens out systemís dynamics and re-enforcing CL amplifies dynamics of systemís behavior. Type of CL depends on the quantity of negative CR: odd quantity of negative CR forms a balancing CL and even quantity of negative CR forms a re-enforcing CL. Elements not included in CL are exogenous and should be determined by analytic during simulation.
3. Development of FD. At this step, CLD should be transformed into FD. A parameter, influenced by a lot of other parameters by use of positive and negative CR should be picked out as a level. Special FD parameters called flaws cause levels to change. Extra FD parameters can be used if needed: constants, flows, tables etc.
4. Determination of parameters and test simulation. At this step analytic should determine parameters of the modeling system. It is viable to determine relative magnitude of the main CL and set modelís parameters based on it. It is also appropriate to check systemís behavior with the boundary values of parameters because insiderís behavior is often obvious with this edge values. Sometimes it is viable to debug the model at the level of one or several elements. Then a test simulation should be carried out. This simulation should give visual information, depiction of insiderís potential behavior, which approves or refutes modelís adequateness.
Insiderís behavior is quite different for different threats. Therefore every threat should be modeled separately.
Insider threats classification based upon [2, 4-7] is listed in Table 1.
Table 1 Ė Insider threats classification
|
Insider threat |
Insiderís motivation |
Insiderís suppose of dismissal |
Internal collusion |
External collusion |
|
IT-sabotage |
Disgruntlement |
Sometimes |
No |
No |
|
IT-espionage |
Money Disgruntlement |
No |
No |
Yes |
|
Manager fraud |
Money |
No |
No Social engineering |
No |
|
Non-manager fraud |
Money |
Not |
No |
Sometimes |
|
Theft of IP for business advantages |
Business advantages Disgruntlement |
Yes |
No |
Yes |
|
Theft of IP for business advantages with accomplices |
Business advantages
|
Yes |
Yes |
Yes |
|
Unintentional negligent insider |
No |
No |
No |
No |
|
Unintentional manipulated insider |
No |
No |
No |
Social engineering |
Some definitions should be introduced.
Insider Ė a current or former employee, contractor, or business partner who has or had authorized access to an organizationís network, system, or data and who, through action or inaction causes harm or substantially increases the probability of future serious harm to the confidentiality, integrity, or availability of the organizationís information assets, IT-infrastructure, or financial systems [2, 7]. Intentional insider causes harm with intent and is motivated. Unintentional insider causes harm unintentionally.
IT-sabotage Ė information security threat, an insiderís use of information systems of organization to direct specific harm at an organization or an individual [2].
Theft of IP for business advantages Ė information security threat, an insiderís use of information systems of organization to steal confidential or proprietary information from organization to use to take to new job, to get a new job, or to start a business [6].
IT-fraud Ė information security threat, and insiderís use of information systems of organization for the unauthorized modification, addition, or deletion of an organizationís data (not programs or systems) for personal gain, or theft of information that leads to an identity crime (e.g., identity theft or credit card fraud) [5].
IT-espionage Ė information security threat, an insiderís use of information systems of organization to collect and pass confidential information to an external party (competitive organization or foreing contry) for advantage of external party without an intend to leave the ogranization. If external patry is a competitive organization, a term ęindustry espionageĽ should be used. If external party is a foreign country, a term ęinternational espionageĽ should be used.
On basis of researches [2-8] and information about insider threat incidents from the other open sources a typical scenario of insider crime and common relationship diagram of insider threat are developed.
Motivation is a key element for crimeís commitment. Motivation is interconnected with collusion for IT-espionage, theft of IP for business advantages alone and with accomplices and part of non-manager fraud threats. Insider checks if the privileges he possesses enough to carry out the crime and resorts to internal collusion (for theft of IP for business advantages with accomplices) or manipulating subordinates (for manager fraud). Insiderís behavior can cause a harm to organization but gives an opportunity to get an information about crimeís commitment. Organization can response to potential or committed crime in different ways. One of sanctioning ways is to dismiss insider. But dismissal can be a motive for commitment of the crime for such threats as IT-sabotage and theft of IP for business advantages alone or with accomplices.
Main elements of the modeling systems are listed in Table 2 and common relationship diagram in Fig.1.
†
Table 2 Ė Main elements of the modeling system and their relationship
|
Ļ |
Element |
Influencing elements |
|
1 |
Insiderís motivation |
Organizationís reaction Collusion Insiderís dismissal |
|
2 |
Organizationís reaction |
Organization receiving information |
|
3 |
Organization receiving information |
Insiderís behavior |
|
4 |
Insiderís technical privileges |
Organizationís reaction Collusion Insiderís dismissal Insiderís behavior |
|
5 |
Collusion |
Insiderís motivation Insiderís technical privileges |
|
6 |
Organizationís damage |
Insiderís behavior |
|
7 |
Insiderís dismissal |
Insiderís motivation Organizationís reaction |
|
8 |
Insiderís behavior |
Insiderís motivation Insiderís technical privileges |
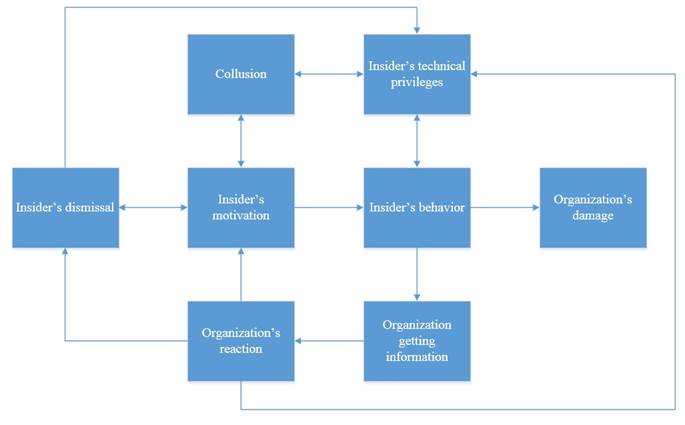
Fig. 1. Common relationship diagram for insider treats
3. Visualization of theft of intellectual property for business advantages
On basis of [6] and information about insider threat incidents from the other open sources an insiderís portrait (Table 3) and common features of theft of IP for business advantages (Table 4) were developed.
Table 3 Ė Insiderís portrait for theft of IP threat
|
Ļ |
Attribute |
Description |
|
1 |
Position held |
Software developer, researcher, client manager, manager (thieves usually hold technical position but donít appear to be privileged users) |
|
2 |
Attack methods |
Technically simple within legal privileges |
|
3 |
Nature of actions |
Stealing of confidential information: IP, software, khow-how, business plans, client bases, physical equipment |
|
4 |
Crimeís duration |
1 (uncommonly 2 or more) month before disposal |
|
5 |
Crimeís disclosure |
Message from clients Message from non-technical employees Sudden appearance of competitive organization Information security monitoring and audit Data loss protection systems |
Table 4 Ė Common features of theft of IP treat
|
Ļ |
Common feature |
Element |
|
1 |
The majority of thieves steal information related to their work; frequently they have taken part in this information development. As far as investment of insider into information and organization grows, feeling of entitlement grows too. |
Insiderís motivation |
|
2 |
Disgruntlement is typical for thief of IP for business advantage, who acts alone |
Insiderís motivation |
|
3 |
Insider typically doesnít carry out any planning or preparation |
Insiderís motivation |
|
4 |
The majority of thieves had signed a non-disclosure agreement. Organization should remind employees about non-disclosure agreements and responsibility for theft of IP during periodic information security training. |
Insiderís motivation |
|
5 |
Insiders typically do not consider theft of IP for business advantages as a crime. The theft happens during one month before discharge and insider typically does not have some specific plane for usage of the stolen information. |
Insiderís motivation Insiderís dismissal Insiderís behavior |
|
6 |
Insider acts alone and can make an attempt to cover up his tracks |
Insiderís behavior Organization receiving information |
|
7 |
Copy of a large amount of information to external network or to remote device can be an indicator of ongoing crime. Sudden appearance of competitive organization can be an indicator of a committed crime. Organization can get an information about ongoing or committed crime from its employees, insiderís colleagues or manager, or clients, which insider can use for his advantage. |
Organization receiving information |
|
8 |
Volume of theft tends to recede if insider gets to know about organizationís suspicions |
Insiderís motivation Insiderís behavior Organization receiving information Organizationís reaction |
|
9 |
Volume of theft tends to grow if insider covers up his tracks |
Insiderís motivation Organization receiving information Insiderís behavior |
Simulation environment Vensim PLE was used to develop CLD and FD. Vensim is intended for complex dynamic systemís investigation and is free for scientific needs. Vensim notation is listed in Table 5.
Table 5 Ė Systems dynamics diagram notation
|
Parameterís notation |
Explanation |
|
|
Variable or constant |
|
|
Level |
|
|
Flow, causing change of level |
|
|
Positive CR |
|
|
Negative CR |
|
|
Logical CR Ė Logical dependence expressed as a logical function |
|
|
ęGhostĽ variable. Auxiliary element, link to a variable given in brackets. Should be used to simplify diagramís exterior. |
CLD for theft of IP for business advantages is represented on Fig.2.
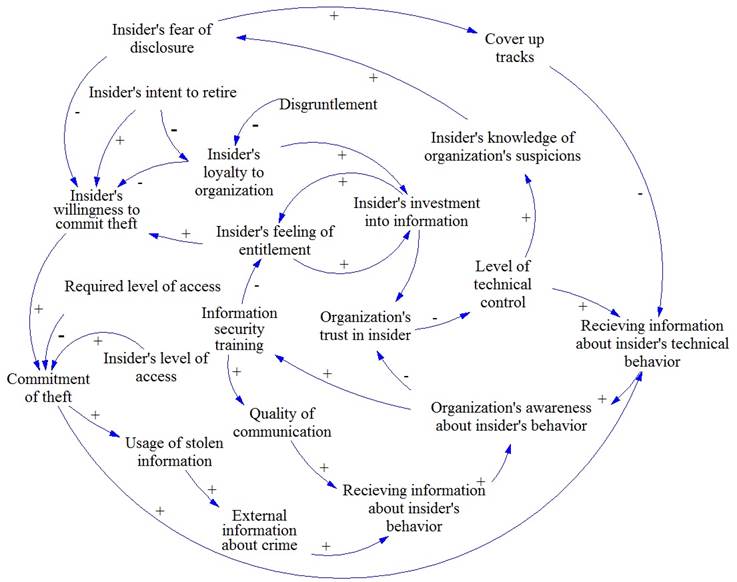
Fig. 2. CLD for theft of IP for business advantages
The following parameters were transformed into levels after analysis: ęInsiderís investment into informationĽ, ęInsiderís willingness to commit theftĽ, ęInsiderís feeling of entitlementĽ, ęEmployees awareness about information securityĽ, ęOrganizationís trust in insiderĽ, ęOrganizationís awareness about insiderís behaviorĽ.
FD for theft of IP for business advantages is depicted on Fig. 3.
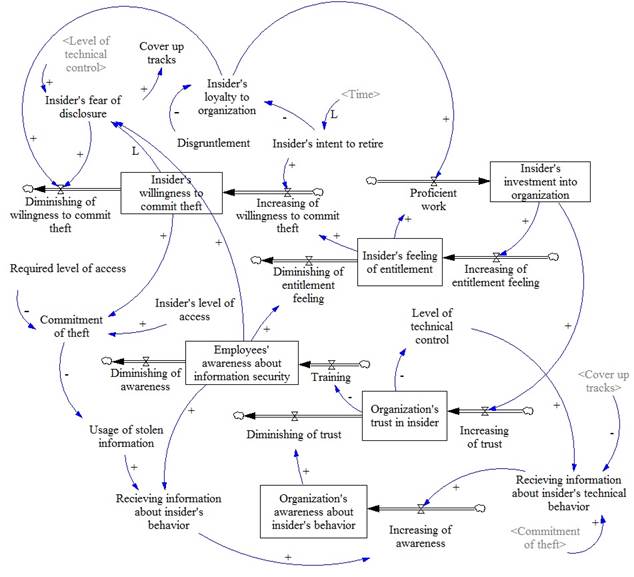
Fig. 3. FD for theft of IP for business advantages
Let us run a simulation with getting of visual information for theft of IP for business advantages threat alone. Firstly, let us set a low value for the Insiderís disgruntlement parameter. Insiderís willingness to retire (external collusion of foundation of own company) appears on the 30 day of simulation. Nevertheless, despite of the fact that insiderís feeling of entitlement achieves its maximum value on the 53 day of simulation, the theft has not been committed due to high level of insiderís loyalty (Fig. 4).
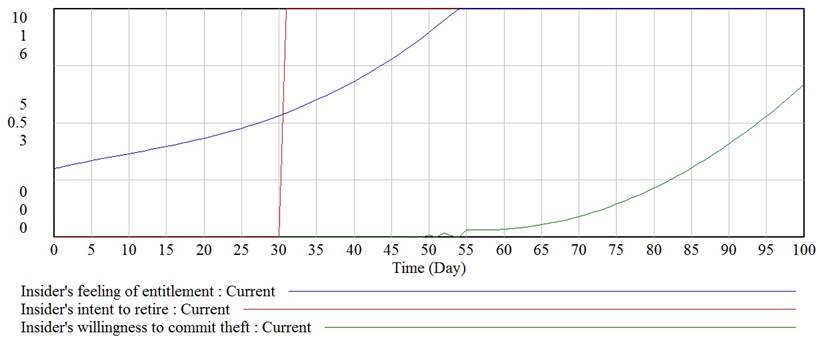
Fig. 4. Willingness to commit theft and feeling of entitlement with low value of disgruntlement
Let us run a simulation again using high value of insiderís disgruntlement. This time, despite of insiderís feeling of entitlement does not reach its top, theft is being committed due to insiderís low loyalty. (Fig. 5).
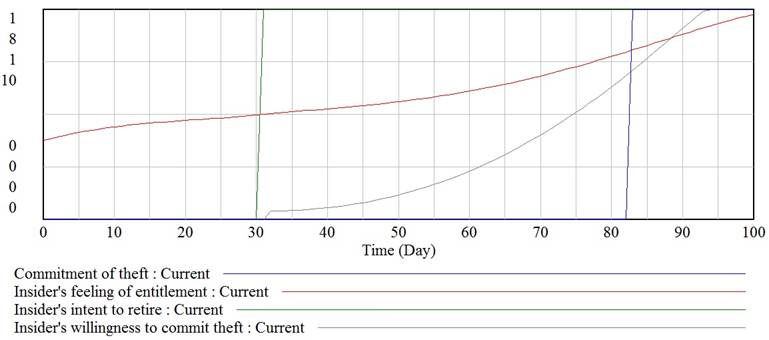
Fig. 5. Willingness to commit theft and feeling of entitlement with high value of disgruntlement
4. Visualization of theft of intellectual property for business advantages with accomplices.
On basis of [6] and information about insider threat incidents from the other open sources an insiderís portrait (Table 3) and common features of theft of IP for business advantages with accomplices (Table 4) are developed.
Table 6. Insiderís portrait for IP theft with accomplices threat
|
Ļ |
Attribute |
Description |
|
1 |
Position held |
Software developer, researcher, client manager, manager (thieves usually hold technical position but donít appear to be privileged users) |
|
2 |
Attack methods |
Insider does not have sufficient privileges to get access to the information. This causes him to hire accomplices. |
|
3 |
Nature of actions |
Stealing of confidential information: IP, software, khow-how, business plans, client bases, physical equipment |
|
4 |
Crimeís duration |
1 (uncommonly 2 or more) month before disposal |
|
5 |
Crimeís disclosure |
Message from clients Message from non-technical employees Sudden appearance of competitive organization Information security monitoring and audit Data loss protection systems News about usage of stolen information |
Table 7. Common features of theft of IP with accomplices treat
|
Ļ |
Common feature |
Element |
|
1 |
The majority of thieves steal information related to their work; frequently they have taken part in this information development. As far as investment of insider into information and organization grows, feeling of entitlement grows too. |
Insiderís motivation |
|
2 |
Disgruntlement is not typical for thief of IP for business advantage with accomplices |
Insiderís motivation |
|
3 |
Volume of theft tends to recede if insider gets to know about organizationís suspicions |
Insiderís motivation Insiderís behavior Organization receiving information Organizationís reaction |
|
4 |
Volume of theft tends to grow if insider covers up his tracks |
Insiderís motivation Organization receiving information Insiderís behavior |
|
5 |
Volume of theft tends to recede in case of long planning since probability of disclosure by organization increases |
Insiderís motivation Insiderís behavior Organization receiving information |
|
6 |
The more insider invest into planning the harder is for insider to resist from stealing |
Insiderís motivation
|
|
7 |
If insider has a lack of privileges, he tries to hide accomplices. Before it he typically tries to get access himself. |
Collusion Insiderís behavior |
|
8 |
Copy of a large amount of information to external network or to remote device can be an indicator of ongoing crime. Sudden appearance of competitive organization can be an indicator of a committed crime. Organization can get an information about ongoing or committed crime from its employees, insiderís colleagues or manager, or clients, which insider can use for his advantage. |
Organization receiving information |
|
9 |
The majority of thieves had signed a non-disclosure agreement. Organization should remind employees about non-disclosure agreements and responsibility for theft of IP during periodic information security training. |
Insiderís motivation |
CLD for theft of IP for business advantages is represented on Fig.6.
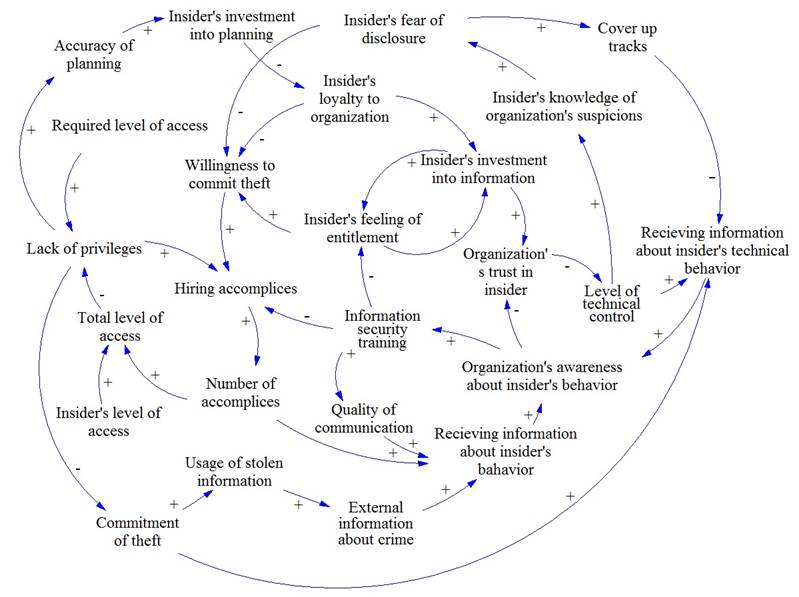
Fig. 6. CLD for theft of IP for business advantages with accomplices
The following parameters were transformed into levels after analysis: ęInsiderís investment into informationĽ, ęInsiderís willingness to commit theftĽ, ęInsiderís feeling of entitlementĽ, ęEmployees awareness about information securityĽ, ęOrganizationís trust in insiderĽ, ęOrganizationís awareness about insiderís behaviorĽ, ęNumber of accomplicesĽ.
FD for theft of IP for business advantages with accomplices is depicted on Fig. 7.
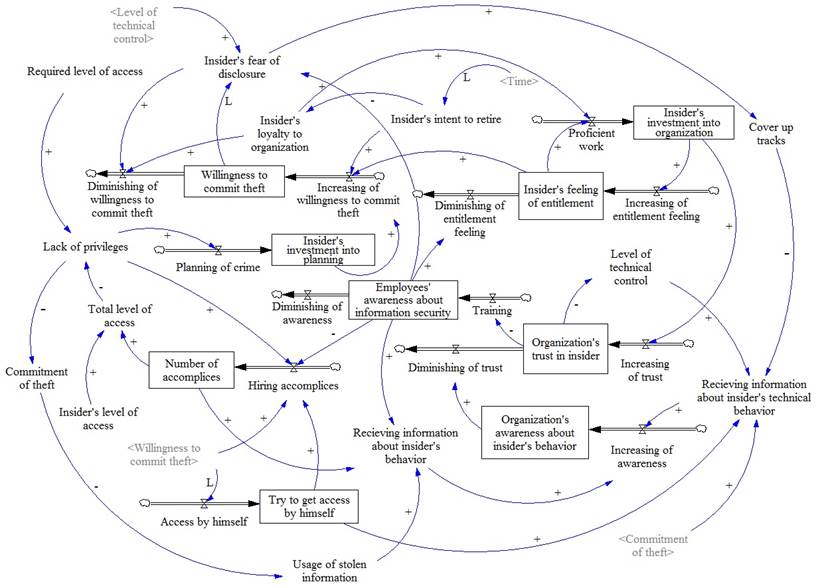
Fig. 7. FD for theft of IP for business advantages with accomplices
Let us run a simulation with getting of visual information for theft of IP for business advantages with accomplices threat. Willingness to retire (external collusion or foundation of own company) appears on the 30 day of simulation, unsuccessful attempt to access information by himself happens on 33 day of simulation and stealing of IP with accomplices happens on 46 day of simulation. These events are depicted as step functions on Fig. 8, 9 and 10.
Hiring of accomplices is depicted on Fig. 8. Within the simulation insider succeeds to hire 3 accomplices.
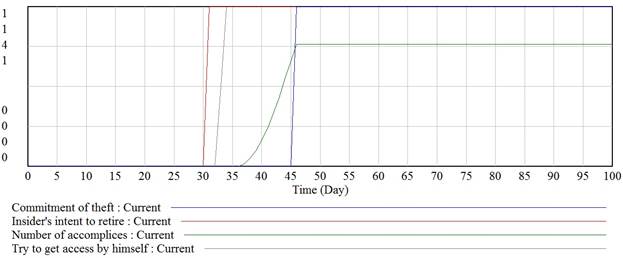
Fig. 8. Hiring accomplices
Organizationís trust in insider demonstrates constant growth during first 40 days of simulation. Organizationís awareness about insiderís behavior reaches significant level only after insiderís usage of stolen information (Fig. 9).
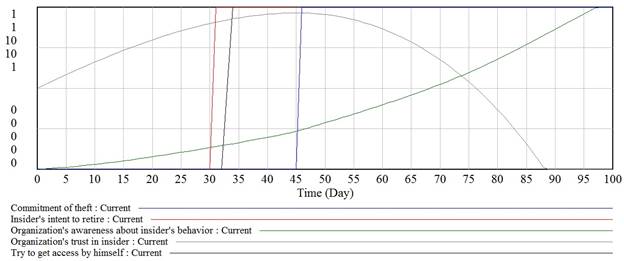
Fig. 9. Organizationís trust in insider and awareness about his behavior
The crime appeared to happen due to high initial level of trust in insider by organization. It caused lack of technical control upon insiderís actions and lack of employeesí awareness about information security (Fig. 10).
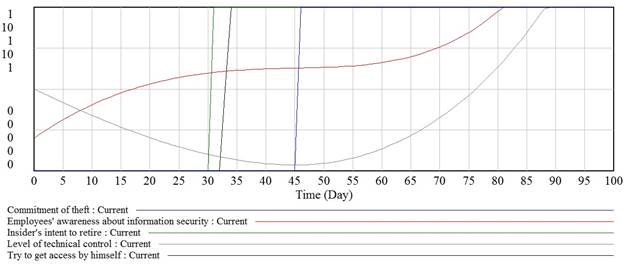
Fig. 10. Level of technical control and employeesí awareness about information security
Let us carry out another simulation using low initial level of organizationís trust in insider. This time organization succeeded in adequate suspicious activity detection and taking countermeasures such as amplify technical control level and conducting information security training. No crime was committed (Fig.11).
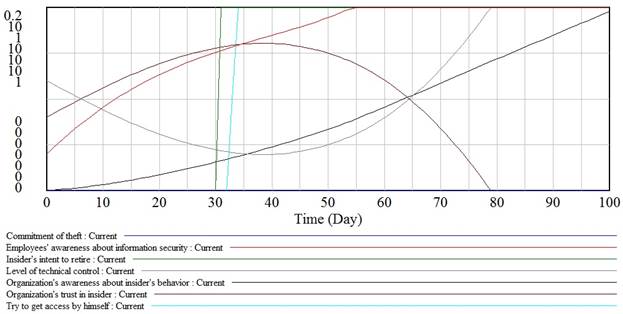
Fig. 11. Theft of IP with accomplices visualization with low value of trust in insider
5. Conclusion
The paper considers a method of decision -making support in field of countermeasure to insider threats with the help of insiderís behavior visializaion with system dynamics modeling appliance. A common relationship diagram for insider threats and forecasting behavioral models for theft of intellectual property threats for business advantages alone and with accomplices are developed. Designed visual information is obtained with the help of models. Visual information can help manager to make a decision for insider threat countermeasure with minimum damage for an organization.
References
1. J. Forrester. Osnovy kibernetiki predprijatija [Fundamentals of Cybernetics of the enterprise]. - M .: Progress, 1971 [In Russian]
2. Silowash G., Cappelli D., Moore A., Trzeciak R., Shimeall T.J., Flynn L. Common Sense Guide to Mitigating Insider Treats 4th Edition. Ė Software Engineering Institute. CERT Program, 2012;
3. Zajcev A.S., Maljuk A.A. Issledovanie problemy vnutrennego narushitelja [Study of the problem insider]. - M .: Herald RSUH. - 2012. - N 14. - pp. 114-134 [In Russian]
4. Band S.R., Cappelli D.M., Moore A.P., Shaw E.D., Trzeciak R.F. Comparing Insider IT Sabotage and Espionage: A Model-Based Analysis. Ė Software Engineering Institute. CERT Program,2006;
5. Cummings A., Lewellen T., McIntire D., Moore A.P., Trzeciak R. Insider Threat Study: Illicit Cyber Activity Involving Fraud in the U.S. Financial Services Sector. Ė Software Engineering Institute. CERT Program,2012;
6. Moore A.P., Cappelli D.M., Caron T.C., Shaw E., Trzeciak R.F. Insider Theft of Intellectual Property for Business Advantage: A Preliminary Model. Ė First International Workshop on Manager Insider Security Threats (MIST 2009), Purdue University, West Lafayette, 2009
7. The CERT Insider Threat Team. Unintentional Insider Threats: A Foundational Study. Ė Software Engineering Institute, CERT Division, 2013;
8. PERSEREC. Espionage and Other Compromises of National Security. Case Summaries from 1975 to 2008. Ė Monterey, CA: Defense Personnel Security Research Center, 2009.

