VISUAL REPRESENTATION OF THE MODEL OF SECURITY THREATS FOR CLOUD-BASED INFORMATION SYSTEM
D.S. Simonenkova, A.N. Veligura
National Research Nuclear University MEPhI (Moscow Engineering Physics Institute), Moscow, Russian Federation
dasha-simonenkova@yandex.ru, vg_2000@mail.ru
Contest
2. Functional capabilities of CBIS
3. The model of intruder in CBIS
4. Threats and vulnerabilities of reference CBIS model
5. Visual representation of CBIS’s threats model of information security
6. Software architecture of the complex
Abstract
One of the key steps at the decision of scientific problems in the field of information security is to create actual model of security threats and model of intruders. This paper describes a new method for the visual representation of the model of security threats and model of intruders, which simplifies the work of researchers at this stage, without reducing the quality of the results.
The main advantages of the proposed method are described. The scheme of software system that allows to implement the developed technique for constructing and displaying the threat model in information security in cloud-based information system is described too.
Keywords: Visual representation, Petri net, information system, cloud computing technology, threat model.
1. Introduction
The providing of confidentiality, integrity and availability of information processed in information system (IS) is one of the most important conditions for the successful functioning of any IS.
It is necessary to pay special attention to the design of information security systems in the IS to ensure an adequate level of security of information
The construction of threat model and model of intruders of information security is the starting point for the design.
In accordance with [1], the threats model of information security can be represented as a physical, mathematical, descriptive representation of the properties or characteristics of information security.
Based on existing techniques [2], [3] the building of threat models is a process of drawing up tables which containing a list of possible threats, security assessment and determination of actual threats. As practice shows this approach to the modeling of threats is a difficult and complicated for the subsequent perception.
The model of intruder in accordance with [4] is an abstract (formalized or non-formalized) a description of the intruder of access control rules.
In the scientific literature, as well as regulatory guidance documents can be found various methods of classifying intruders, thus, the intruder model is informal.
Addition of threat models and intruders by their visual representation would greatly simplify their understanding and further application, without compromising the quality of the results. At the present time, in the public domain can be found in [5-9] in which a greater or lesser extent used a visual representation of IS’s individual functioning of attacks on them in solving various problems
In this paper describe the developed method of construction and the visual representation of the threats model of information security in the information system, built using the technology of cloud computing (CBIS). As an example for describing technique was chosen CBIS because of their rapid development and growth in popularity in recent years. Currently, there is no generally accepted method of constructing a model of threats to CBIS. Consequently, this paper describe the process not only the visual representation of the threat model in information security of CBIS, but also developed a technique of constructing a model of threats model of information security of CBIS.
The process of building a threat model of information security in CBIS and its visual representation, can be represented as a sequence of steps.
Step 1. Identify and visual presentation features of CBIS.
Step 2. Identify and visual representation of the level of intruder’s functionality capabilities of information security in CBIS.
Step 3: Identification and visualization vulnerabilities and threats of information security that can potentially exist in CBIS.
Step 4: Identification and visualization of current security threats in CBIS.
2. Functional capabilities of CBIS
In order to develop a methodology for constructing a threats model of information security and a visual display of it. It is necessary to understand architecture and functionality of system accurately.
The conducted analysis of reference models for constructing CBIS versions of NIST [10], Microsoft [11], IBM [12] and Microsoft TechNet [13] showed that in these models the levels of virtualization and services are not detailed, while the construction of the threat model data levels have a major role. Due to this fact, a new CBIS model is proposed, in which the indicated levels have been described in the best way to build threat models. The proposed reference CBIS model can be presented in accordance with Figure 1.
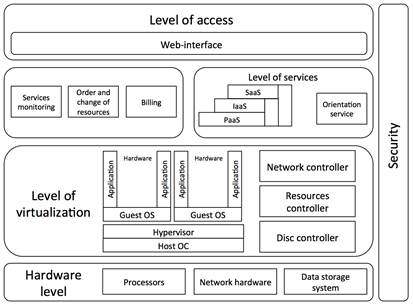
Fig. 1. The proposed reference CBIS model
The proposed CBIS model, unlike those studied, gives a more detailed view on the components of a virtualization layer and services and on the way they interact with each other. It provides a better understanding of the CBIS structure in terms of its information security.
The proposed model for cloud computing has two main operating entities: subscriber of the cloud and operator of the cloud, both of whom can act in a particular role and take appropriate action.
In accordance with Figure 1, the proposed CBIS model can have five levels: access, services and automation, virtualization and management, hardware level and security level.
The access to administrative functions of CBIS for administrators and cloud self-service functions for subscribers are provided at the level of access to CBIS.
The operator of cloud services provides such services as IaaS, SaaS and PaaS at the level of services and automation; this level also includes orchestration service. Management of the provided services (allocation, delivery, etc.) is also at this level.
The orchestration service performs the functions of monitoring, management, planning, resources computing and resource storage.
The level of virtualization and management is the basic level, through which physical resources are converted into virtual machines, networks and drives for data storage. Also virtual resources are monitored on this level. Resource management is affected at the service level by service orchestration.
The level of physical resources is the basis level of CBIS architecture, which includes all the computing resources and storage and network equipment located in the data centre.
The level of security covers all levels of the CBIS model. Thus on each of levels of CBIS: physical resources, virtualization and managements, services and automation and access level are applied protection frames (technical, organizational-legal), approaching for each concrete level.
For building and displaying threat model in CBIS should be formulated a systematic explanation of the features CBIS.
Description of CBIS’s functionality capabilities
Functionality of the proposed CBIS model construction can be described in terms of the theory of Petri nets.
This representation allows us to describe the functioning of the system and the conditions in which CBIS potential vulnerabilities exist in most detail and clearly.
Definition. The Petri net is a quadruple, C = (P, T, I, O). P= {p1, p2 ,…, pn} − a finite set of places, n ≥ 0. T = {t1, t2 ,…, tn} − a finite set of transitions, m ≥ 0. Plurality of positions and plurality of transitions are disjointed, P ∩ T = ∅. I: T→P∞ input function – a mapping from transitions to sets of positions. O: T→P∞ − output function – a mapping from transitions to sets of positions.
Simple representation of the Petri net is based on two fundamental concepts: events and conditions. Events are actions taking place in the system. Occurrence of events manages the position of the system. The position of the system can be described by a variety of conditions [14].
The position into which the CBIS is transmitting at the moment t, is described by a set of parameters:
- ct – confidentiality;
- it – integrity;
- at – accessibility, such that ct, it, at ∈ {0,1}.
ct=1 (similar to it=1, at=1), if in a given position the confidentiality (integrity and availability, respectively) of information processed in the CBIS. If privacy is violated and/or integrity and/or availability parameters assume the zero value ct=0, it = 0, respectively, it=0 and/or at=0. Thus, the state of the system at the moment the transition t can be represented by st = (ct, it, at) ∈ S.
The state of the system in which the vector st = (1, 1, 1) is called safe state (S+). The state in which at least one of the parameters is zero is considered an unsafe or unacceptable condition (S-).
S+∪ S- = S,
where S is the set of all possible states of the system.
Visual representation of CBIS’s functionality capabilities
For a visual representation of functionality of the proposed CBIS model and illustration of the concepts of the theory of Petri nets is convenient to use a graphical representation of a Petri net.
The Petri net structure is a set of positions and transitions. According to this the graph of Petri net has two types of nodes. ○ circle is a position (state of CBIS) and strap │ is a transition.
Description of functionality Petri network was carried out in accordance with the proposed CBIS model shown in Figure 1. Thus the constructed Petri net consists of 249 positions, and 314 transitions (P = {p1, p2, ..., p249}, T = {t1, t2, ..., t314}).
The number of positions and transitions is determined by functionality of selected CBIS models.
In view of the fact that the entire network is composed of a large number of elements, Figure 2 in this article displays only the initial portion of the constructed network (subgraph of Petri nets of CBIS reference model), that renders the running CBIS and creation of the account by the CBIS subscriber).
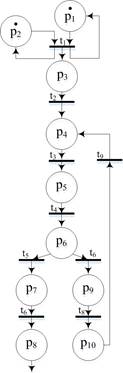
Fig. 2. Running CBIS and creation of an account
This network includes the following states and transitions:
position p1 – availability of power;
position p2 – standard software and OS are present;
position p3 –standard OS and software are working;
position p4 – data is not entered;
position p5 – data is entered;
position p6 – updated data;
position p7 – data is entered correctly;
position p8 – account was created;
position p9 – entered data is not true;
position p10 – account is not created;
transition t1 – loading of standard software and operating systems;
transition t2 – run CBIS;
transition t3 – data entry;
transition t4 – data validation;
transition t5 – outputting the result;
transition t6 – account creation;
transition t7 – outputting the result;
transition t8 – error output;
transition t9 – request to re-enter data.
Marking μ is an assignment of features to the states of Petri nets. A feature is a primitive notion of Petri net (similar to positions and transitions). Features are assigned (we can assume that they belong to) positions. The number and position of features, when the Petri net is affected, may vary. Features are used to determine whether the Petri net is functioning.
On a graph, Petri net features are represented by small dots in circles, which in their turn represent the position of the Petri net.
Initial marking M0 of this graph is defined as follows:
M0 (p1) = M0 (p2) = M0 (p11) = 1, M0 (p3),…, M0 (p10), M0 (p12) ,…, M0 (p252) = 0,
or, in vector form
M0=(1,1,0,0,0,0,0,0,0,0,1,0,…,0).
3. The model of intruder in CBIS
It is necessary to define the intruders of information security in IS for threats model of information security construction after determining the functionality of the system
The model of intruders described in the guidance document Gostekhkomissiya Russia [15] can be used as an intruder’s model in this work.
An entity who has access to work with the standard tools CBIS regarded as the intruder.
Intruders of CBIS classified by level of the opportunities offered to them by standard tools of the system. There are four levels of these opportunities. Each level includes the functionality of the previous one.
The first level defines the lowest level of opportunities for dialogue in CBIS - running tasks (programs) from a fixed set of implementing a prescribed function of information processing.
Example of intruder who has the first level of functionality can be external intruder. Such an attacker can execute an attack on the level of access to CBIS, manipulate available interface elements for access to CBIS.
The second level is determined by the ability to create and run their own programs with new features for processing information.
Example of intruder who has the second level of functionality can be subscriber of CBIS. Subscriber of CBIS has access to the web interface, and with it - to the functions of control in CBIS on the level of service (running virtual machines, their removal, place files in the repository CBIS etc.). Intruder of second level has access to a self-service level in full.
The third level is determined by the ability to control the operation of CBIS, that is exposure to basic system software, and the composition and configuration of its hardware.
Example of intruder who has a third level of functionality can be administrator of CBIS. The intruder of this level has access to the service level (monitoring, billing, order and change resources) in its entirety.
The fourth level is determined by the volume of all people’s opportunities who design, implement and repair hardware CBIS until the turn of the computer equipment of their own hardware with new features for processing information.
Example of intruder who has a fourth level of functionality can be technical specialist of CBIS. This type of intruder has access on the level of physical resources. He has the ability to connect to a CBIS’s local area network own computer equipments, interact with CBIS’s equipment on the network level.
Visual representation of the level of intruder’s of information security functionality
Visual representation of intruder is based on the level of its functionality. For each of the 4 levels of intruder is released subgraph of Petri net describing the state CBIS for which the offender may have an impact. Example of a visual representation of intruder’s levels is presented in Figure 3. Figure 3 shows the subgraph of Petri nets of reference CBIS model due to large size of the entire graph.
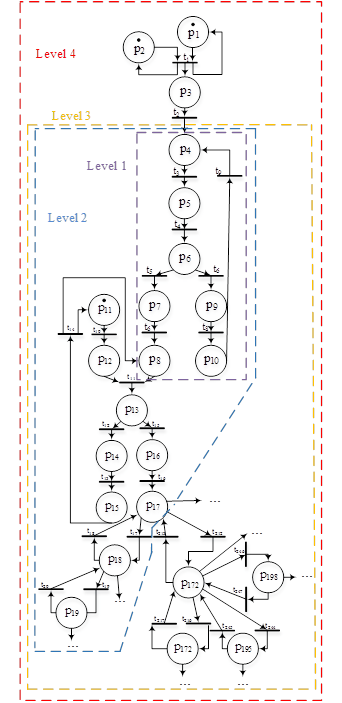
As seen in Figure 3, the intruder of 4th level can affect on any state in CBIS.
The intruder of 3rd level can affect on any state in CBIS except in states which are connected with exposure on the level of physical resources.
The intruder of 2nd level can influence only on the state of the system, available to subscribers CBIS.
The intruder of 1st level can only interact with public elements CBIS.
4. Threats and vulnerabilities of reference CBIS model
The next step of the construction of the threats model of information security in CBIS is drawing up a list of threats and vulnerabilities of information security, which can potentially exist in the system with a given set of features.
The set of threats T and set of vulnerabilities V were separated.
The set of threats T can be described as follows:
T = (I, V, St),
where:
- I – the level of the intruder, which can realize the threat;
- V – the set of vulnerabilities, the exploitation of which leads to the successful implementation of the threat;
- St – the set of state vectors which describe the unsafe state in which the system enters if the threat successfully implemented at time t.
The set of vulnerabilities V can be described as follows:
V = (R, Pt),
ãäå:
- R – the set of recommendations to remove the vulnerabilities;
- Pt – the set of states in which vulnerability may exist.
Visual representation of vulnerabilities
After compiling a list of threats and vulnerabilities, they must be displayed on the graph of Petri net which describes the functionality of the base model CBIS.
Positions which can be potentially vulnerable are marked in red. Conclusions about the existence of vulnerabilities in each state of the Petri net was done on the basis of a detailed analysis of the various CBIS models held while writing this paper. In the event of the successful operation of such vulnerabilities, the system enters an unsafe condition.
An example of a visual representation of vulnerabilities can be represented as shown in Figure 4.
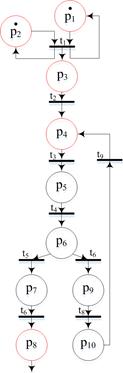
Fig. 4. Vulnerabilities of CBIS
Figure 4 shows the subgraph of Petri nets of reference CBIS. Likewise on the Petri net of reference model CBIS applied all vulnerabilities that could potentially exist in CBIS without the use of data protection facilities.
5. Visual representation of CBIS’s threats model of information security
By combining the visual representations of features of CBIS, levels of capability intruders, list of vulnerabilities in one scheme, we obtain a reference model of information security threats in CBIS.
Drawing of threats on the graph of Petri net of reference model CBIS is not considered on this stage of work. In the future, when building software package that allows implement the described methodology, vulnerability information will be stored in the database.
Visual representation of threats model of information security of CBIS describes the most popular functionality of CBIS such as: vulnerability, which can potentially exist in CBIS, level of intruder’s functionality who can exploit certain vulnerabilities. Visual representation of threats model of information security of CBIS can be represented as shown in Figure 5.
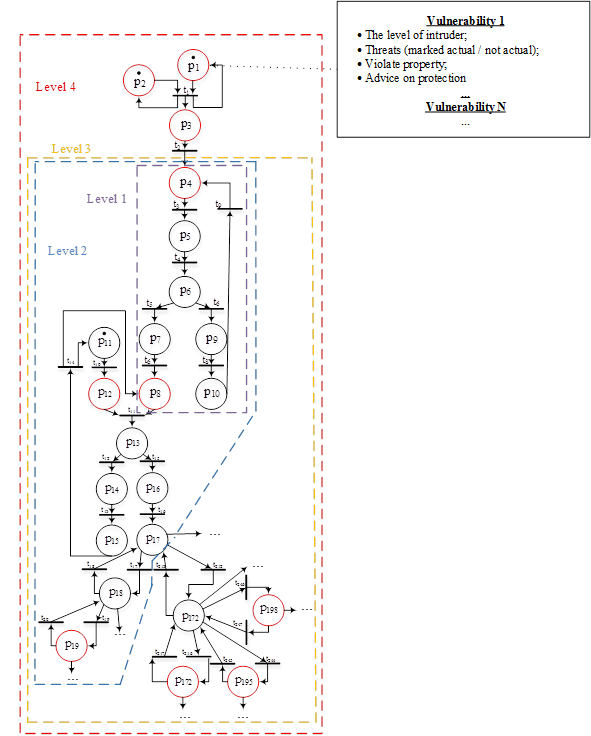
Fig. 5. Reference threats model of information security of CBIS
It is necessary to visualize the process of functioning investigated CBIS by constructing a graph of Petri net which describing the functionality of the investigated CBIS for construct a threats model of information security of investigated CBIS. Construction of the graph done by copying subgraphs of Petri nets of reference CBIS model which describing the functionality which implemented in the study CBIS.
Then compares the visual representation of threat model of information security in reference CBIS with a visual representation of features of investigated CBIS, taking into account the data protection facilities used in the latter. The result of this comparison is a visual representation of the threats that are relevant to the study CBIS.
For speed up and simplify the process of constructing and displaying threat model of information security in CBIS in accordance with the method which has been described has been developed software package.
6. Software architecture of the complex
Figure 6 shows the architecture of the complex allowing implementation of the developed technique.
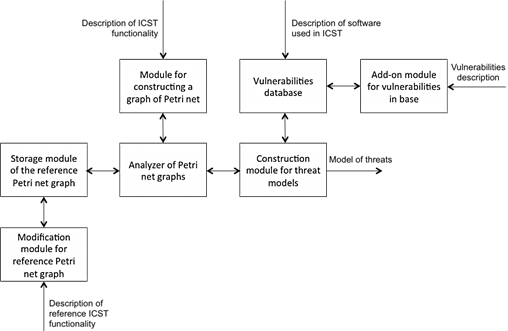
Fig. 6. Software architecture of the complex
The choice of modules included in the system is based on the functions to be performed by the software package in order to apply the developed technique. Those functions include the construction of the Petri net graph, storage of reference Petri net graph, as well as its complements if necessary, storage of known vulnerabilities of software used for CBIS constructing, adding new vulnerabilities, aggregation of all the data needed to construct a CBIS threat model and a visual display of the CBIS threat models. The following modules have been allocated based on this description.
A module for constructing a Petri net graph allows the construction of such a graph for the system under investigation by selecting, from the list, functions implemented in the system.
Storage module of the reference Petri net graph allows for the storage of a matrix representation for further comparison with the graph representation of the Petri net system under investigation
List of relevant threats can be obtained by comparing the functionality of the investigated CBIS, modeled by the Petri net, and some input parameters (used remedies) with the reference model.
The analyzer of Petri net graphs provides the following steps:
1. Ñomparison functionality reference and investigated models CBIS.
2. Identification of:
· states investigated CBIS in which can potentially exist vulnerabilities
· intruders who can exploit vulnerabilities
· potential threats that can be realized by the intruders;
· violated properties;
· recommendations.
3. Determination of actual threats based on the data about information security devices in the investigated CBIS
4. Addition of actual threats based on the identifying vulnerabilities that exist in software which is used for building CBIS
Modification module for reference Petri net graph allows changes to be made in the reference graph: add/edit or delete new functional blocks. Thus, this technique can be applied to any CBIS
The vulnerabilities database contains vulnerabilities of most popular products used to construct the virtualization layer of CBIS. For example, VMware vSphere, VMware vFabric Application Director, Microsoft Hyper-V, Microsoft System Center Operation, etc. Currently the base consists of about 230 vulnerabilities.
The vulnerabilities database is implemented using the product Microsoft Office Access 2007. The choice of the product is due to the ease with which it can integrate the vulnerabilities database with other modules of software which implement the developed methodology of constructing models of CBIS security threats.
Each vulnerability is described by presenting the level of potential danger.
The degree of potential danger is evaluated by CVSS technique [16] based on the base vector
Along with the development of cloud technologies and new means to implement cloud computing services, new vulnerabilities in software will undoubtedly be used at the level of virtualization and virtualization management.
Add-on module for vulnerabilities in base allows the addition of information about newly discovered vulnerabilities in operating systems, hypervisors and software used in CBIS.
Thereby add-on module allows maintainance of a database of vulnerabilities to date and to provide relevant information about the vulnerabilities in the most popular operating systems and software used in CBIS.
The construction module for threat models aggregate information from the analyzer of the Petri net graph and vulnerabilities database and provides the user of the program with detailed information about existing and potential vulnerabilities, offenders, those able to exploit the vulnerabilities, and the threat posed by offenders in the event of their successful operation of a particular vulnerability. An example of a visual representation of the threats model of information security in CBIS obtained at the output of the program is shown in Figure 5.
7. Conclusion
This paper considers the actual problem of constructing threats model of information security and intruders of information security in CBIS with the possibility of visual representation. Visual representation of threats model of information security and intruders of information security in CBIS has several advantages:
- visibility of transition from one state to another state of CBIS (visual display of allowed and forbidden transitions);
- visibility of presentation of the level of intruder’s functionality;
- visibility of presentation of vulnerabilities that can be exploit by intruders depending of the level of his functionality
Thus, the author's method of visual representation of threat threats model of information security in IS makes it easy to identify:
- states of the system in which vulnerability can exist;
- threats that can be realized with a successful exploitation of existing vulnerabilities;
- level of functionality of the intruder, who can realize the threat;
- properties that would be infringed in the implementation of threats.
Thus, the described method simplifies the researcher to construct à threats model of information security and intruders of information security in IS. While the process of building these models is especially important during the design phase of data protection facilities in the IS. In the course of further work under the consideration of the topic is planned testing of the developed technique. As the object of study is expected to use a hybrid cloud - public cloud, which can be dynamically allocated and freed segments to create a rented private clouds.
References
1. GOST R 50922-2006. Information Security. Basic terms and definitions. – Moscow: Federal Agency on Technical Regulating and Metrology, 2006 – 8 p.
2. Basic model of security threats while processing personal data in information systems of personal data: The Order of FSTEC of Russia 15.02.2008 [Electronic resource] // ConsultantPlus [Official website]. Access mode: http://base.consultant.ru/cons/cgi/online.cgi?req=doc;base=LAW;n=99662 (accessed: 15.02.2015).
3. Methods of determining the actual threats to the security of personal data during their processing in personal data information systems: The Order of FSTEC of Russia 14.02.2008 [Electronic resource] // ConsultantPlus [Official website]. Access mode: http://base.consultant.ru/cons/cgi/online.cgi?req=doc;base=LAW;n=77814 (accessed: 15.02.2015).
4. Guidance document. Protection against unauthorized access to information. Terms and definitions. The Order of GosTekhKomissiya of Russia 30.03.1992 [Electronic resource] // ConsultantPlus [Official website]. Access mode: http://base.consultant.ru/cons/cgi/online.cgi?req=doc;base=EXP;n=513377 (accessed: 15.02.2015).
9. A.V.Lukatsky. Threat model: from static to dynamic. [Electronic resource]: SecurityLab [Official website]. Access mode: http://www.securitylab.ru/blog/personal/Business_without_danger/51986.php (accessed: 15.02.2015).
11. Building a private cloud architecture from Microsoft. [Electronic resource]. Access mode: http://www.winzone.ru/articles/1047 (accessed: 15.02.2015).
12. Introduction and Architecture Overview. IBM Cloud Computing Reference Architecture [Electronic resource]: Document version 2.0 – 28 January 2011 — Access mode: http://dosen.narotama.ac.id/wp-content/uploads/2012/01/Cloud-Computing-Reference-Architecture.doc (accessed: 15.02.2015).
13. The private cloud reference model [Electronic resource]. Access mode: http://technet.microsoft.com/ru-ru/cloud/hh744847.aspx (accessed: 15.02.2015).
15. Guidance document. The concept of protection of computers and automated systems from unauthorized access to information. The Order of GosTekhKomissiya of Russia 30.03.1992 [Electronic resource]. Access mode: http://fstec.ru/tekhnicheskaya-zashchita-informatsii/dokumenty/114-spetsialnye-normativnye-dokumenty/387-rukovodyashchij-dokument-reshenie-predsedatelya-gostekhkomissii-rossii-ot-30-marta-1992-g4 (accessed: 15.02.2015).
16. A Complete Guide to the Common Vulnerability Scoring System Version 2.0 [Electronic resource]. Access mode: http://www.first.org/cvss/cvss-guide.html(accessed: 15.02.2015).